You have been directed to this page because you have responded and clicked a malicious link, which was sent from an email account requesting to change your password.
This phishing exercise has been prepared by TZ-CERT to emulate and provide awareness on phishing attacks. Attackers use social engineering techniques to collect users’ information by tricking them to enter their credentials such as username and password on embedded malicious links.
Please read the tips below!
What is Phishing attack?
Phishing attack is the social engineering technique; it uses email or other types of voice or messaging applications to carry out a message with a ploy to convince the victim to perform some actions. Cyber attacker may send an email that appears to come from a legitimate organisation.
Possible actions associated with phishing include-
- Clicking a link or opening attachment to install malicious software i.e. computer virus, malware.
- Fill-in an electronic form to divulge sensitive information i.e. username and password, credit/debit card number, passport numbers etc. where their credentials are harvested.
How to identify a deceptive phishing email
- Check carefully email address of sender. If you cannot see the address, try to move your cursor over the name of sender to reveal it. Cyber attacker use two tricks : –
- Use a real company/organization name before ‘@’ sign to make it look credible; for example: it@tcra.info
- Use web address/URL which looks similar to the genuine one as described below:
| Genuine url : https://webmail.tcra.go.tz |
| Scam url: https://mail.tcra.info/?rid=atHicqQ |
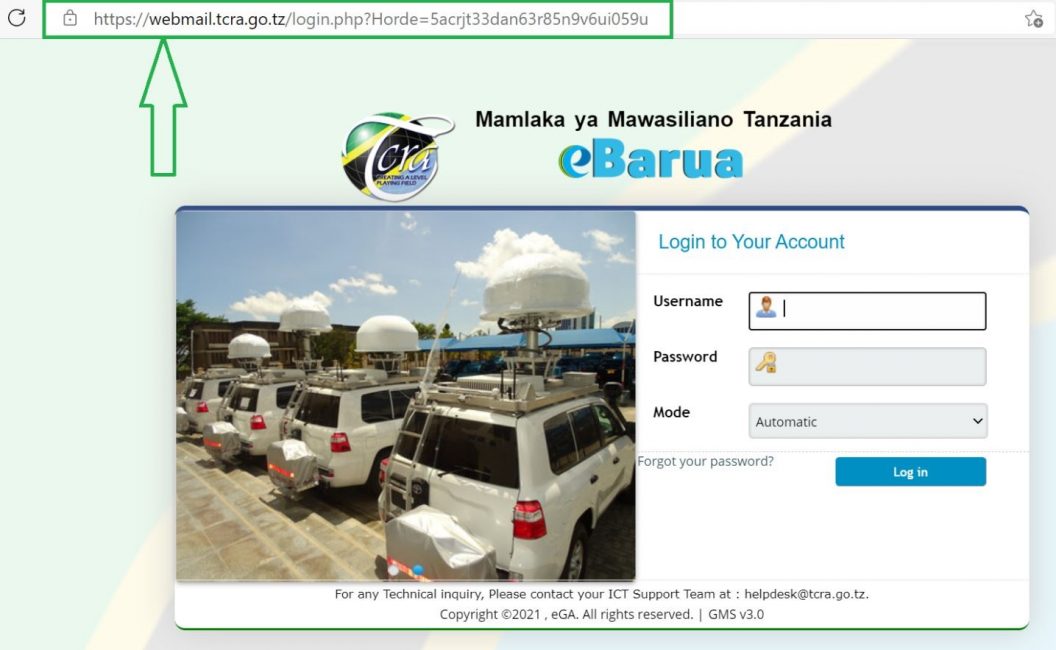
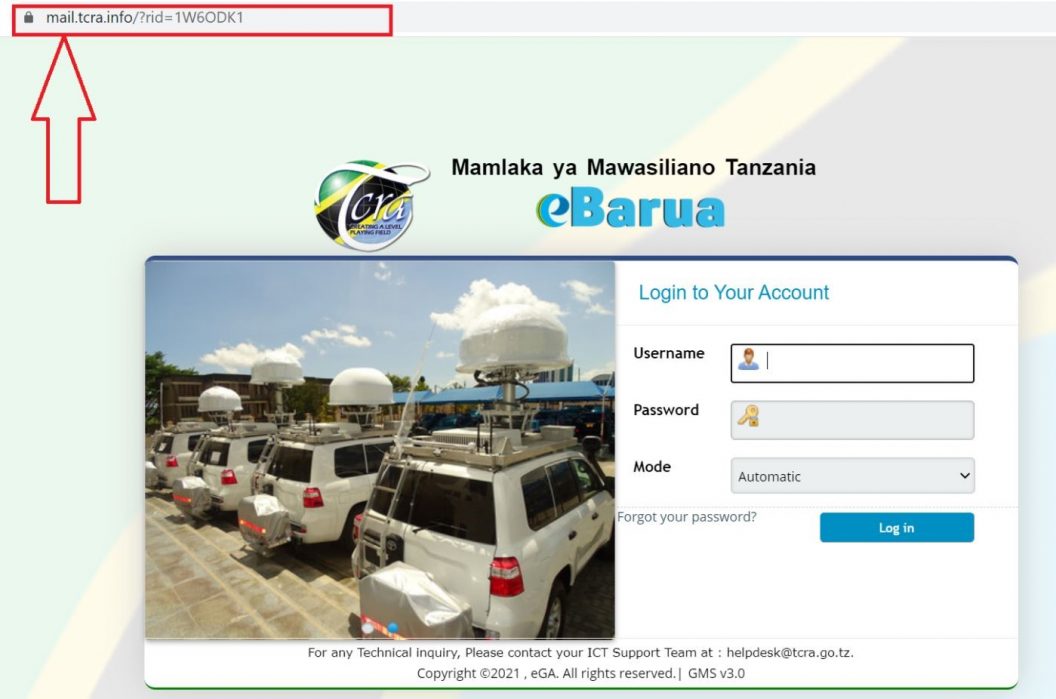
It is worth taking a moment to inspect the underlying links/URL in the address carefully to make sure are the same as a known website address.
2. Suspect email(s) with generic and attractive greetings such as ‘Dear valued customers’. Don’t open any attachment sent with this kind of emails.
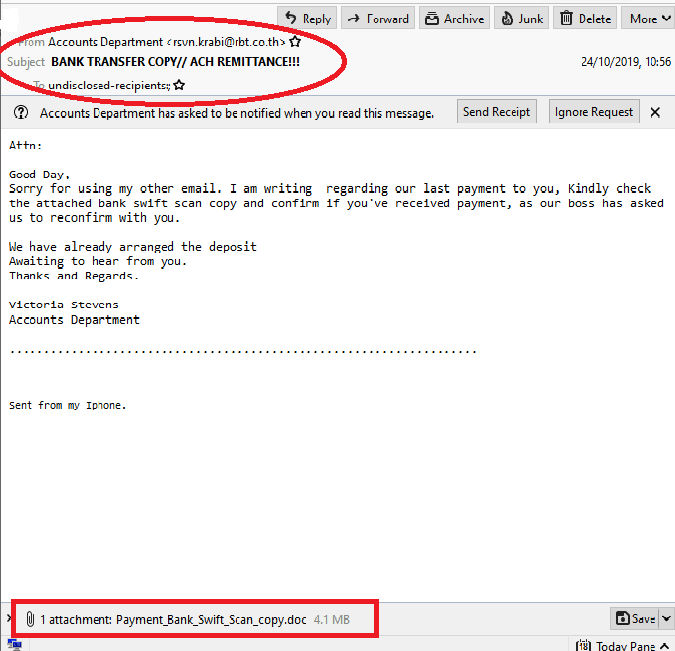
3. Be aware and attentive to details such as spellings, punctuation and grammar.
4. Sense of urgency: Usually cyber attackers prefer to use sentences that come with urgency, conditions and threatening. Their aim is convincing recipients to rush into responding without taking precautions.
For example: –
- “You will be fined if you don’t act now”.
- “If you don’t update your information within 48 hours, your account will be suspended”.


 Tanzania Computer Emergency Response Team
Tanzania Computer Emergency Response Team